▶ Databases are half of the “Double Extortion” schemes
▶ 250K MySQL DBs for sale from 85K victims
▶ 2021 Cybercrime damages predicted to reach $6 trillion
▶ Encrypting data in a Database demonetizes its value

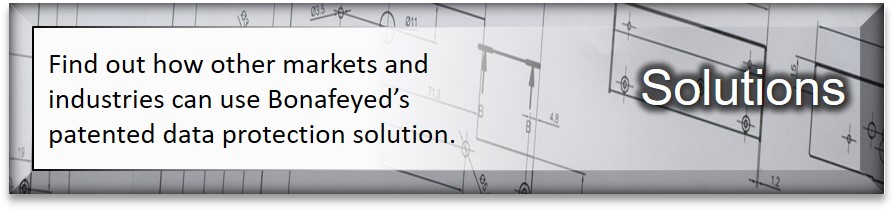
Bonafeyed’s Data-Defined protection approach – safeguards database entries rather than applying an “at-rest” encryption of the entire database or the storage where it resides. This means first encrypting data and then submitting to the database application. By leveraging this approach, the Cy4Secure data security solution is capable of individually encrypting each field or row or column of data. The benefits of protecting the records or individual fields allow not only the highest level of data protection but access control as well as preserving the value of the data.
The question that instantly comes to mind is, how can the database work with encrypted data? The answer is remarkably simple. Database systems do not know the difference between data that is encrypted with Cy4Secure or data that is human readable. Its only concern is that the data meets the entry field’s attributes. If it looks like data, databases can perform their operations such as whole searches and partial searches or sorts. When making queries, the operations are performed using Cy4Secure encrypted versions of the data and the database just searches for the encrypted equivalent version of the data. For instances where arithmetic operations are required on numerical entries, order preserving encryption can be used on numerical fields. Conversely, each PII numeric data entries such as a social security numbers, can be individually encrypted and obfuscated because they are not used in mathematical or sorting operations.
Therefore, individual data fields, records and columns can be encrypted to control access from unauthorized users. This allows broader sharing of its data or records and ensures in the event of a data breach or theft by a bad actor, data remains protected, unavailable, and demonetized.


▶ Nation-State Actors target large SaaS applications
▶ Everyone including the Hackers are in the cloud
▶ Human error is the top contributing threat
▶ SaaS databases are at risk

In May of 2019, CRM cloud giant, Salesforce.com, Inc. (SFDC) service was disrupted when as posted by them, “A maintenance-related single-purpose database script launched at 01:45 UTC on May 17, 2019 mistakenly gave elevated data access permissions to users within an organization.” It was purported by customers and the press; the script gave past and current users of the company's Pardot B2B marketing automation system full read and write access to all data. In other words, an Enterprise’s data was openly available to other companies to examine and query. This unfortunate event is analogous to an insider attack, albeit an accidental one. Nevertheless, whether the SaaS or the cloud host for the SaaS adds another form of vulnerability. Today, a SaaS offers the industry standard data-in-transit and data-at-rest protection technologies, access controls and some optionally offer proprietary onsite security gateway appliances requiring one of these boxes at each customer location. Question is how can customers independently secure their data in a SaaS application without modification and available to remote employees, partners and even clients?


▶ FLE and RLE allow single record/user access encryption
▶ 20% of US, UK, and EU companies are GDPR compliant
▶ Single field/record can be “cryptographically forgotten”
▶ HIPAA can fine up to $429USD per exposed record

The European Union first blazed the trail to protect consumer personal information when the General Data Protection Regulation (EU) 2016/679 or "GDPR" became law on May 25, 2018. The United States quickly followed suit, as each State began rolling out their own regulations. In March of 2018, all 50 U.S. states enacted breach notification laws that require businesses to notify consumers if their personal information is compromised. California lawmakers enacted the California Consumer Privacy Act of 2018 or the “CCPA” June 28, 2018. Others included Alabama with SB 318, Arizona with HB 2145, Colorado with HB 1128, Iowa with HF 2354, Louisiana with Act Number 382, Nebraska with LB 757, Oregon with SB 1551, South Carolina with H4655, South Dakota with SB Number 62, Vermont with H. 764, Virginia with HB 183 and many others followed. California has alreadyCalifornia has already made several amendments, most recently October 11, 2019 and again November 2020 (called CPRA), to their new laws and created additional legislation similar to GDPR.
Many of these data protection acts also stipulate that consumers have the right to be forgotten and to request that any data a company has on them be deleted. There are some limits on what data a business can retain for legal, compliance, and business reasons, but a solution must be in place to timely delete all other information about a consumer.
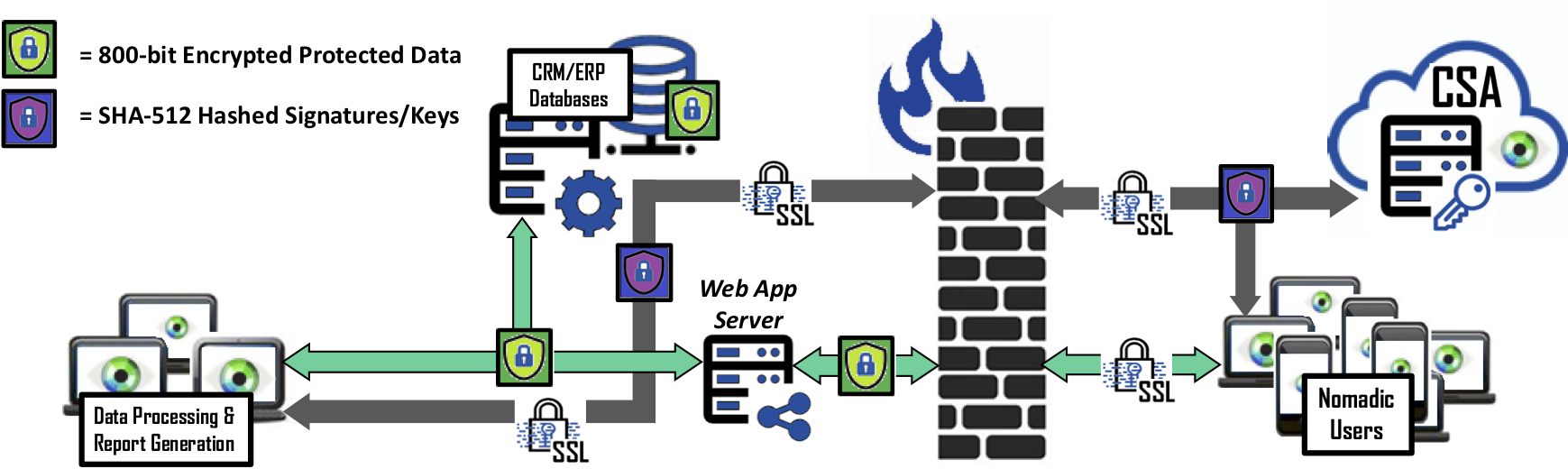
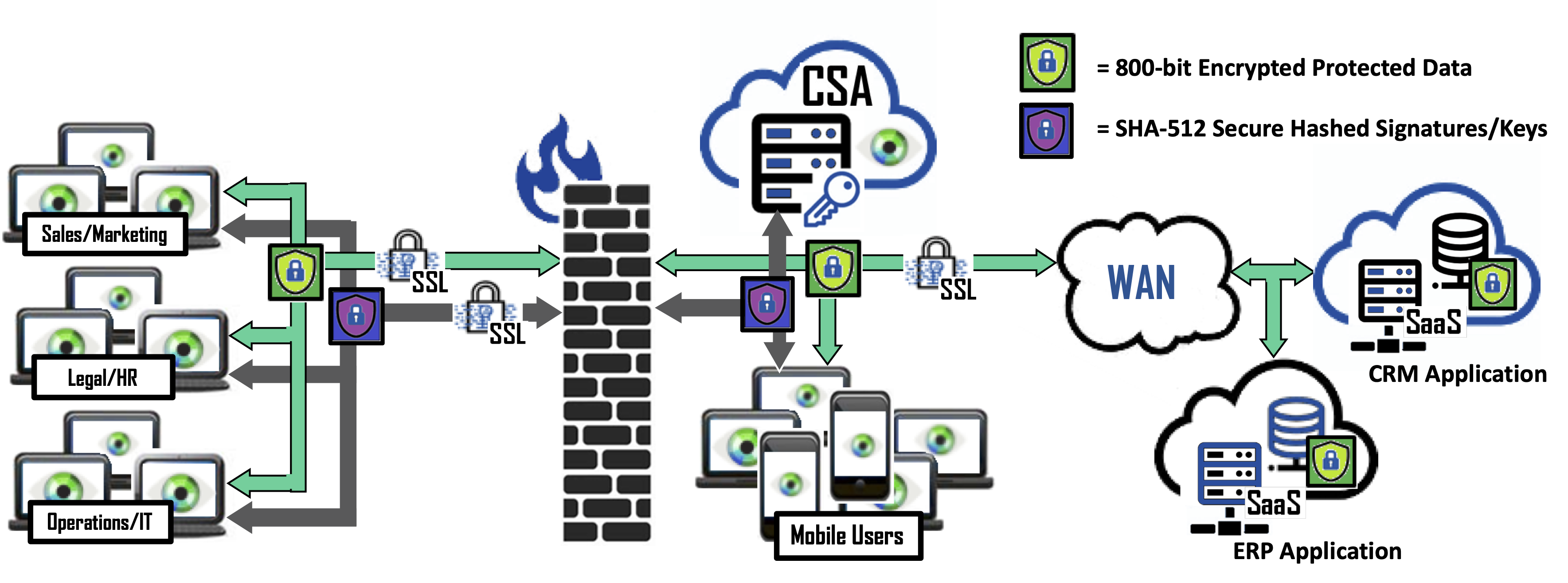
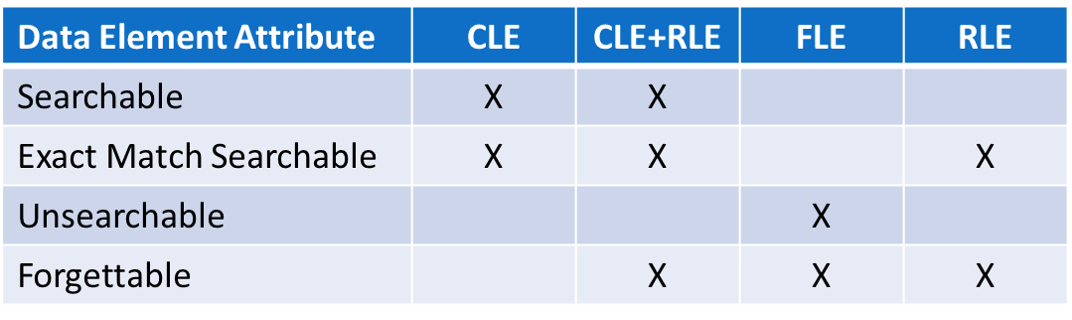
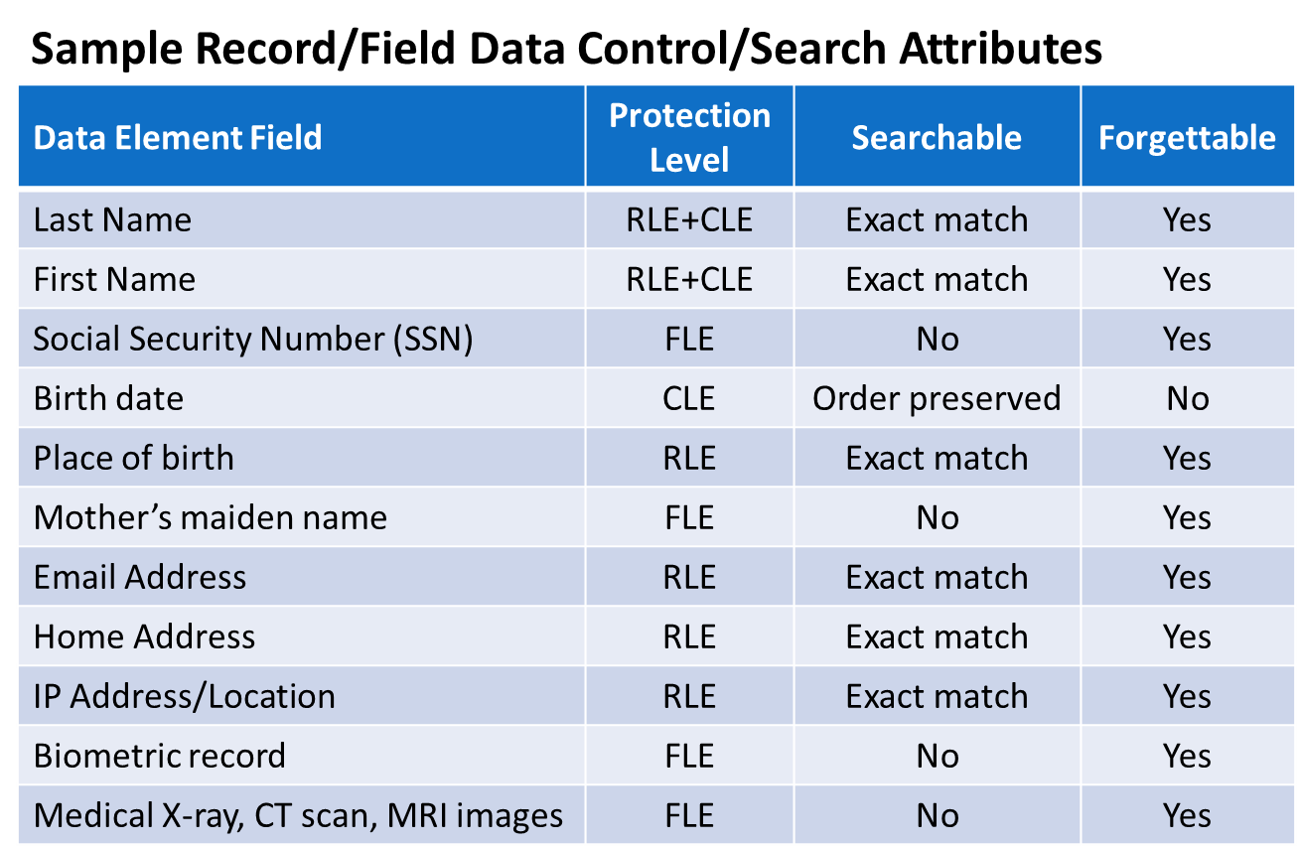
Cy4Secure’s innovative data defined security provides a new dimension for data privacy and data control. A combination of Column, Field and Row level encryption not only protects data but can determine if a single data field of a record or row is searchable or unsearchable in a query while retaining the ability to be forgotten.
Deploying Bonafeyed’s Cy4Secure technology encrypts consumer personal data, in real-time and the data remains protected when accessed by authorized users within an enterprise’s network, or outside by 3rd party partners or mobile devices. In addition, the consumer datasets when placed on backend Business Enterprise systems or in the cloud for collaboration or archival storage remains natively secured. However, when encrypted data is lost, stolen, abandoned, or forgotten, it becomes demonetized ensuring cybercriminals or internal non-authorized users only obtain unintelligible data and permanently inaccessible once the cipher keys to access the data are deleted or retired, which exceeds data protection legislation.
The frequency of breaches also arises from focusing on perimeter security and not on protecting the data itself. Data that remains in the “clear” is vulnerable. Bonafeyed can secure individual data elements, such that any loss of data whether by a mega breach or down to an end-user’s mobile device is mitigated. Traditional security products are just one part of the solution. Since cybercriminals have found quick ways to monetized stolen data, without directly securing and protecting the data, these massive breaches and data exploits will continue to occur.


▶ Lost business is about half the cost of a data breach
▶ Encrypted data has no value to the cyberthieves
▶ It takes millions of keys to open a protected database
▶ Over 300M people impacted by data breaches in 2020

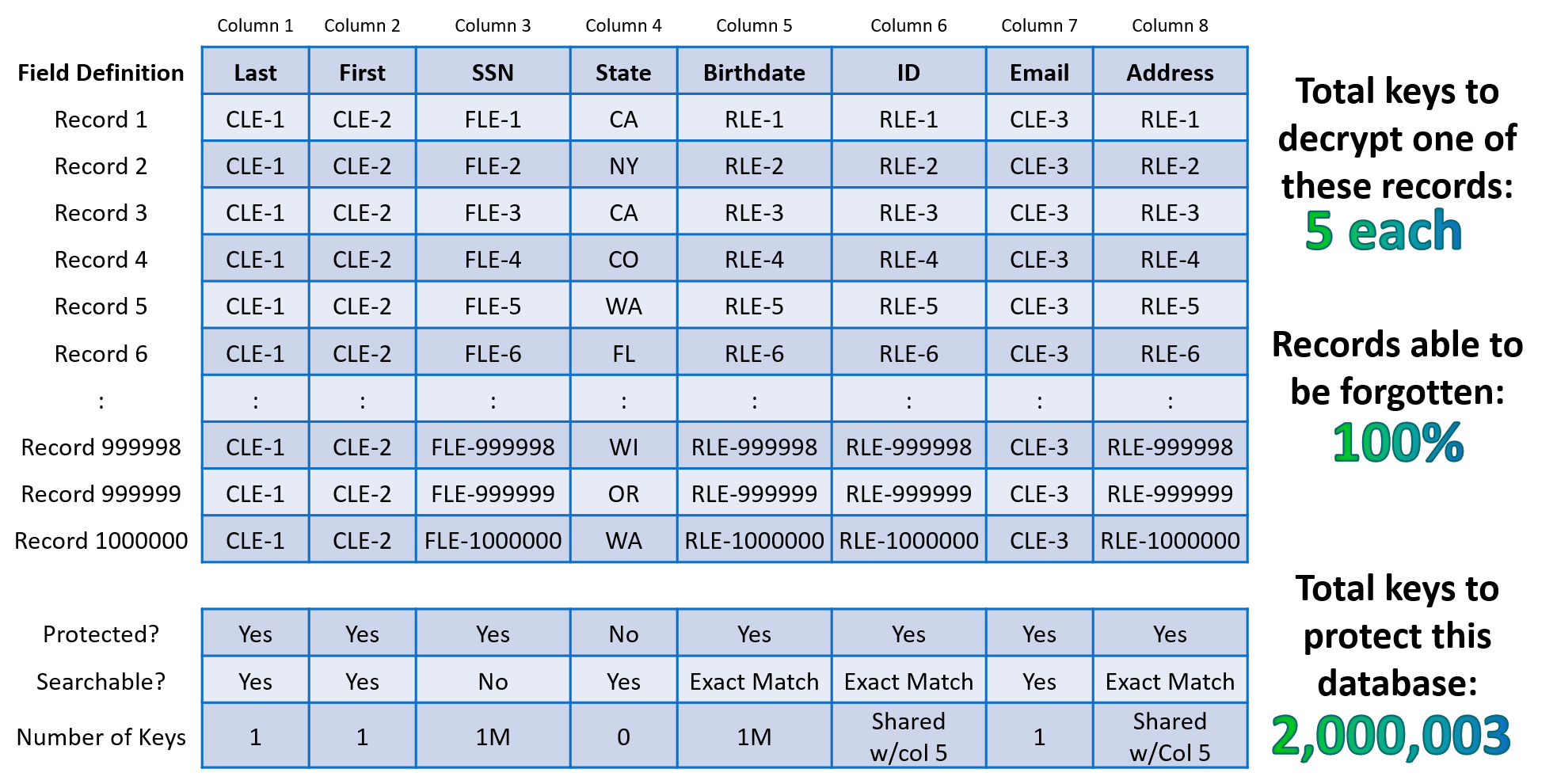
In the case of a ransomware attack, the cybercriminal usually holds hostage the victim’s data for cryptocurrency, promising that once payment is made, they will re-enable access to the data with no guarantees of leaking it. Unfortunately, most of the time, adding insult to injury, cybercriminals not only collect the payment from the victim, but they also place the data on the dark web for the highest bidder. Imagine this being Personal Health Information (PHI). Whoever buys this data can now use it to extort anyone, even a high-profile target like an executive, celebrity or political figure, or worse yet, collect massive amounts of money via fraudulent insurance schemes using patients’ medical reports. Since Bonafeyed focuses solely on protecting the data, even when a cybercriminal hits the jackpot and stumbles into a wide-open database with millions of PHI records, the individual data fields and records remain encrypted requiring multiple keys to access a single record and millions of encryption keys to reveal the entire database.
Now consider another scenario that lately has been breaking many headline news – a cyberattack coming from an organized crime gang with affiliation to an unfriendly country. Today, we are witnessing more cases mentioning the FBI and other agencies helping companies resolve the problem with mixed results. Talk about a serious hostage situation! A quick pay-out to the criminals to get your business back is no longer a valid option and companies are stopped dead on their tracks, causing major headaches due to impact on operations and revenue. Relying on the reaction time of an overworked government agency to assist in the process for paying out the ransom, if allowed, should not be the only option.
When Cy4Secure protected data is lost, stolen, abandoned, or forgotten, it remains secure and becomes permanently inaccessible once access to the encryption keys are removed or retired ensuring cybercriminals or non-authorized users only obtain unintelligible digital data.


▶ Column inclusion (copies) is a feature leakage
▶ Time leakage uses older data for testing
▶ Misconfigured server leads to data leakage
▶ Inadequate security practices result in leakage

- Good ole fashion access management that controls the rights to
retrieve data records or submit queries to a database application.
- Encrypting data while en route to and from a database system.
- Encrypting data before the database management system sends it to
storage and again decrypting once read from storage.
- Obfuscating data in database records.
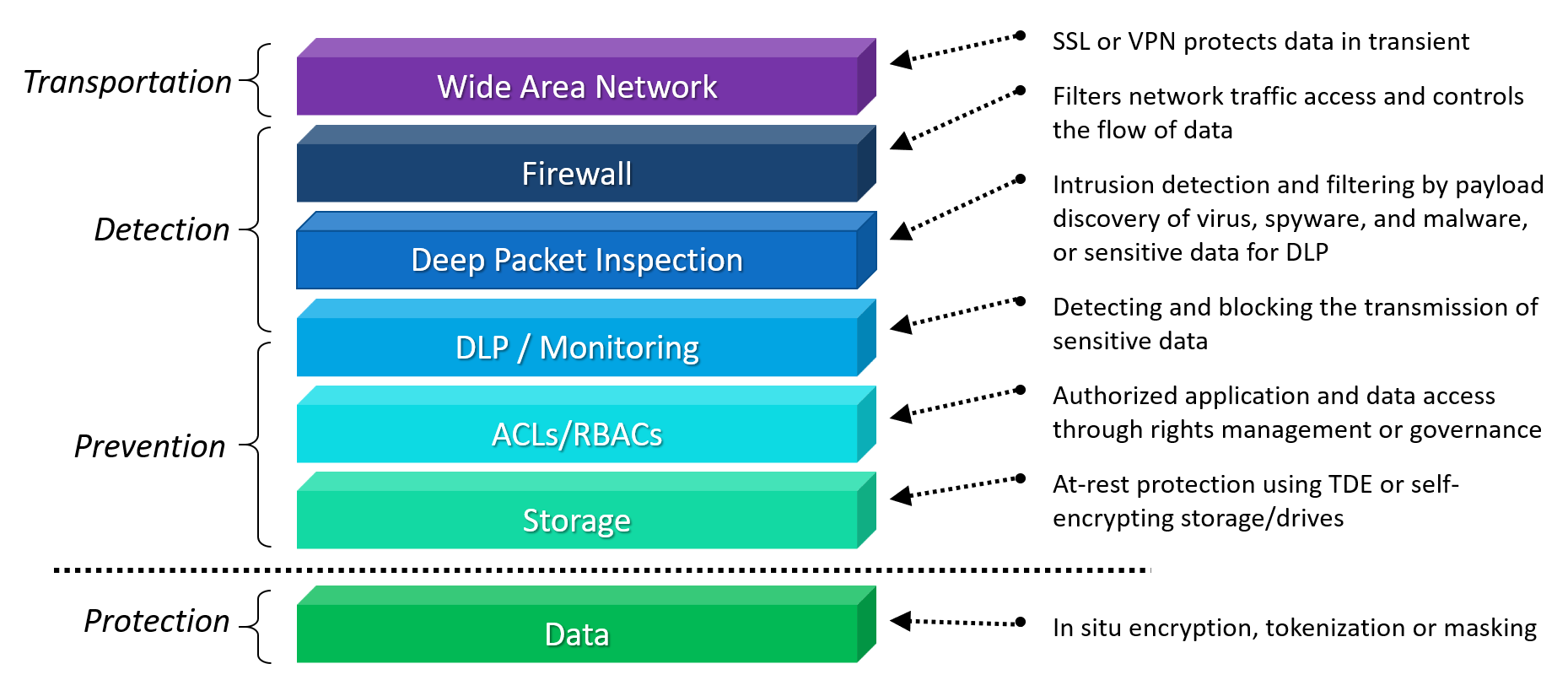
Each of these techniques represents a well understood security layer that attempts to work in concert to accomplish database privacy.
The downside is that security responsibility ends as data leaves an adjacent layer before entering another. Each layer protects the data while transiting that layer. The handoff between layers requires the data to be unprotected.
Access Control
Controlling user access to systems, applications or data comes in two forms: RBAC, role-based access control and ACL, access control levels. In both cases, data records or fields are not specifically encrypted, rather, this security schema limits the availability of data. RBAC controls access to systems or applications based on a user’s status within a domain or an enterprise’s business hierarchy. ACL differs by explicitly limiting access to data either in the form of a file (as with Microsoft’s active directory) or a data field such as Row Level Security (RLS) in a DBMS. If RBAC or ACLs are compromised as is common with phishing attacks, the outcome is the same – the data is freely available in the clear. Data is guarded, not encrypted.
Payload Protection
Whether in motion or at rest, data is treated as an intermediate payload and once delivered is stripped of its protection. Data saved to storage by the database is encrypted by built-in or 3rd party functions known as Transparent Data Encryption (TDE) and is in turn decrypted when pulled from the storage before it is delivered to the database management system. This means data in the DBMS is always in the clear. Now consider when data is sent over networks using TLS/SSL transport protocols. The data is encrypted just before it leaves the machine and stays encrypted while in transit and is immediately decrypted once it arrives at its destination. Again, in both cases, data, whether stored or transported, is delivered in the clear or as plaintext after it exits these security layers.
Data Security
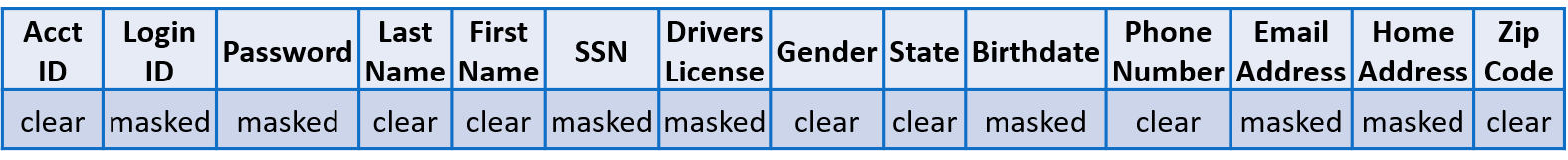
It should be mentioned that obfuscation techniques such as data masking and tokenization are effective, but ultimately just remove information from a database and place it in a data vault, which is typically managed by a 3rd party, for later retrieval. Naturally, you trust that 3rd Party implicitly to keep your data safe. Unfortunately, this approach hinders the ability to perform relational queries and analytics on a database, an important if not critical function to gain insight on data. Conversely, data considered “non-sensitive” in the same database remains in the “clear” such as zip code, race, gender, and date of birth which can be leveraged to distinguish an individual and violates all data privacy regulations.
Masking sensitive data in a database record – partially searchable
Tokenizing sensitive data in a database record – limited searchability
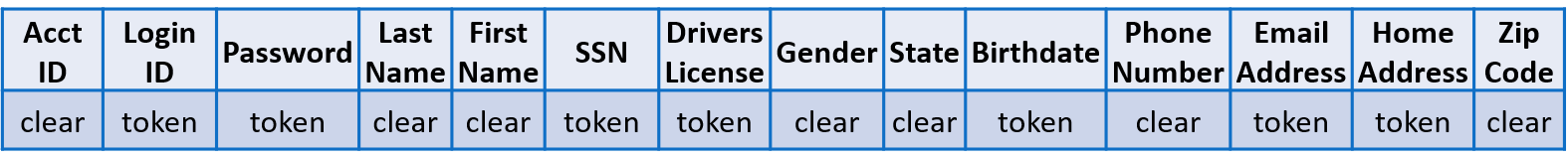
To truly protect data, it should be encrypted and remain encrypted, whether at-rest, in-motion, or in-use. Cy4Secure’s Data Defined Security encrypts all data no matter the size or type. More importantly the data remains encrypted even while in-use by a database. Bonafeyed's technology separately encrypts data fields within a database record yet still allows complete searchability without any changes to the database management system.
Encrypting all data in a database record – fully searchable
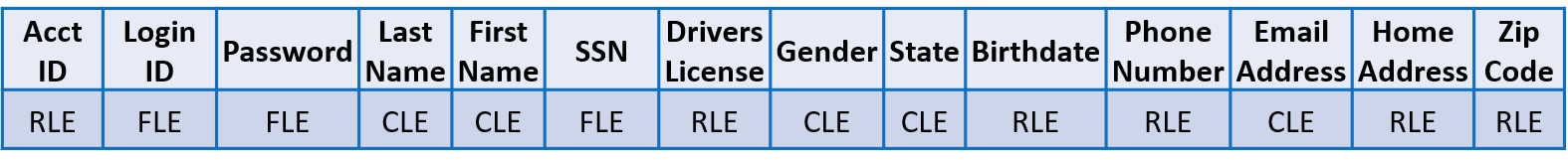
For example, applying column level encryption (CLE) to protect searchable data fields, field level encryption (FLE) for unsearchable, and row level encryption (RLE) to protect all remaining fields within a record, translates into dozens of cryptographic keys to decrypt a single record and 100% data protection coverage. In situ data security is now possible with Cy4Secure, ensuring that breached databases or data leakage of illicitly queried records remain secured and protected.