



▶ Select any combination of predicates and conditions
▶ Fully compatible with search engines
▶ Search structured and unstructured data fields
▶ Works with all Database Management Systems

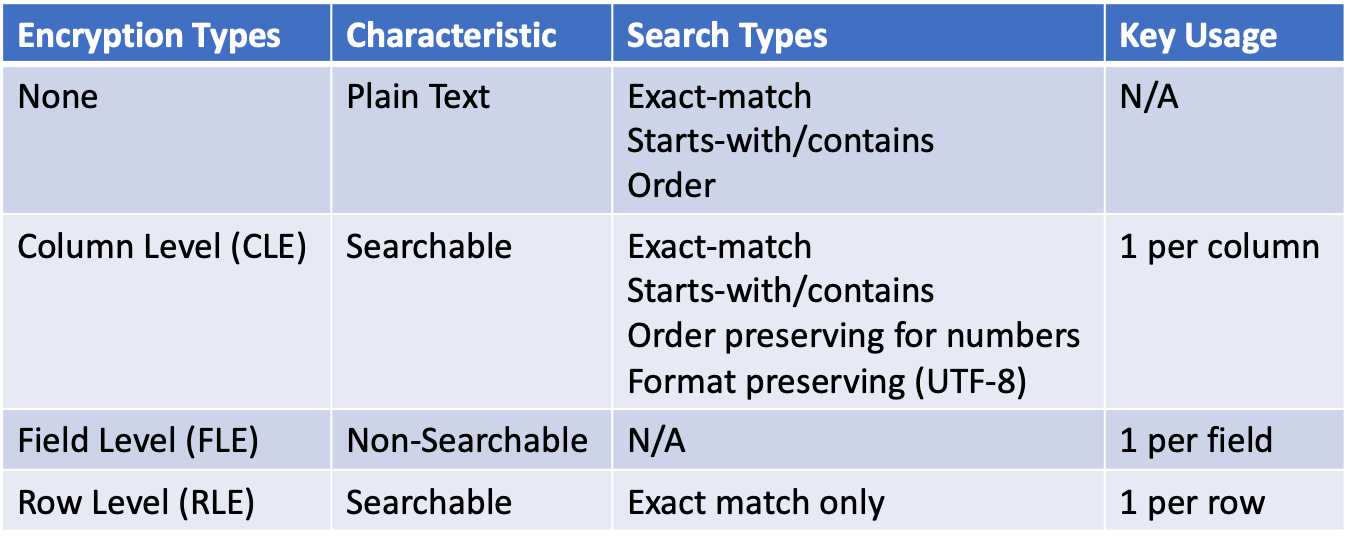
To accomplish this feat, data records are encrypted when entered or updated in a database. DBAs and the Chief Data Officers or CISOs can define the encryption schema for each data field, row, or column using common or different 800-bit or 256-bit encryption keys. Each column can either be encrypted for order preservation or equality search ability, referred to as Column Level Encryption (CLE). Or to protect PHI and PII data fields such as social security numbers, credit card numbers or bank account information, a unique key can be used for each entry for maximum security and is not searchable. This is known as Field Level Encryption (FLE). In addition to innate data protection, a third level of protection is Row Level Encryption (RLE). RLE uses a common key for fields in the same row or record for exact match only searches and provides a legitimate multi-tenant database “row level security”. When combined, Bonafeyed brings a new level of data security that utilizes millions of keys to secure millions of data elements rather than just 1. Yes, millions to secure the contents within a database. This means every field, column or row can be encrypted, requiring many keys to decrypt a single record. Refer to Exceed Privacy Regulations to see how this fine-grain data protection is applied to individual PII and PHI data elements.
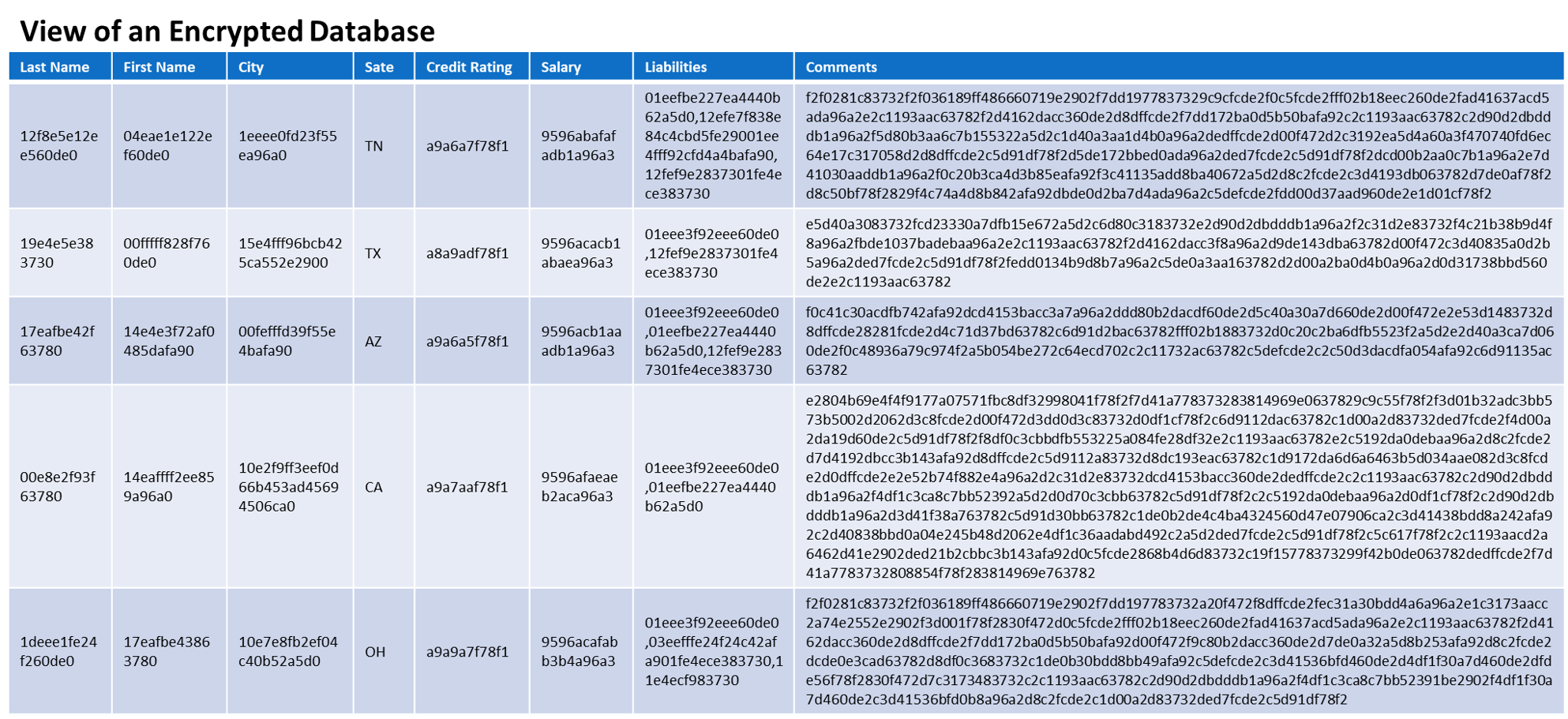
It turns out, a database does not know the difference between data that is encrypted with Cy4Secure or data that is human readable. Its only concern is that it meets the requirements of the field entry. Databases, storing Cy4Secure protected data, can still perform normal operations such as whole searches, partial searches, and groupings. When making queries, the search criteria is encrypted by Cy4Secure at the client and the database executes the query on the encrypted equivalent version of the data for exact match, starts-with, contains, ordered, or ranged. To make this possible, Cy4Secure ensures encrypted data continues to appear as data. Cy4Secure does not impose a specific encrypted data structure prior to sending other than providing the option of generating binary ASCII or hexadecimal output of the encrypted data. Otherwise, encrypted data appears as homogenized group of 1’s and 0’s, or unprintable characters not readily useable by an application. The data can simply be stored directly or with a tag identifying the utilized encryption key. The latter example affords a mixture of both encrypted and non-encrypted data in the same data set. A fast checksum verifies the data is encrypted and can be subsequently (after retrieving a key) decrypted prior to display or use.
In the simplest description, a search is a search. That is, any Cy4Secure encryption operation performed during data entry can likewise be performed on any search criteria. Common grouped and cross-tabulated results can be performed on Cy4Secure encrypted data with the added benefit of generating reports with encrypted data that is only viewable by authorized persons. Deploying Bonafeyed’s Cy4Secure on database applications ensures the data fields within a database are encrypted and only accessible by authorized users. In the event of a breach, the data remains secured and private from cybercriminals or in-network non-authorized users.


