



▶ Protect data behind cloud applications and services
▶ Secure data shared between services
▶ Aggregator platform Cermati.com leaked info of 3M users
▶ Lending app Tokopedia leaked 91M users to the dark web

Finance Use Case: FinTech Customer Information Protection
The Gramm-Leach-Bliley (GLB) Act imposes data security and data-sharing standards on businesses that engage in general categories of ‘‘financial’’ activities. In addition, many U.S. states, New York, New Jersey, Connecticut, Massachusetts and California, have supplemented GLB with the ‘‘money transmitter’’ laws to cover financial technology or “FinTech” companies.
“Financial companies must….ensure the security and confidentiality of customer information and to protect against unauthorized access to or use of that information, both by third parties and your own employees.”
This means GLB places responsibility for data security directly with the board of directors and for public companies, the Sarbanes-Oxley Act makes the CEO and CFO responsible. With alarming frequency, new reports of serious breaches reveal that concentric or layered security architectures based on detection, protection and transportation technologies are simply inadequate. In many cases human error plays the largest role from misconfiguration, fraudulent scams, and even intentional security violations. Making this problem even more complex to solve, leading global Fintech companies are proactively turning to cloud technology in an attempt to meet increasingly stringent compliance regulations. This is not to say the security challenge is not also faced by historical financial companies since they do offer Internet-connected customer services. Nevertheless, any data breach, no matter how small, can result in direct liability to a company and its officers.
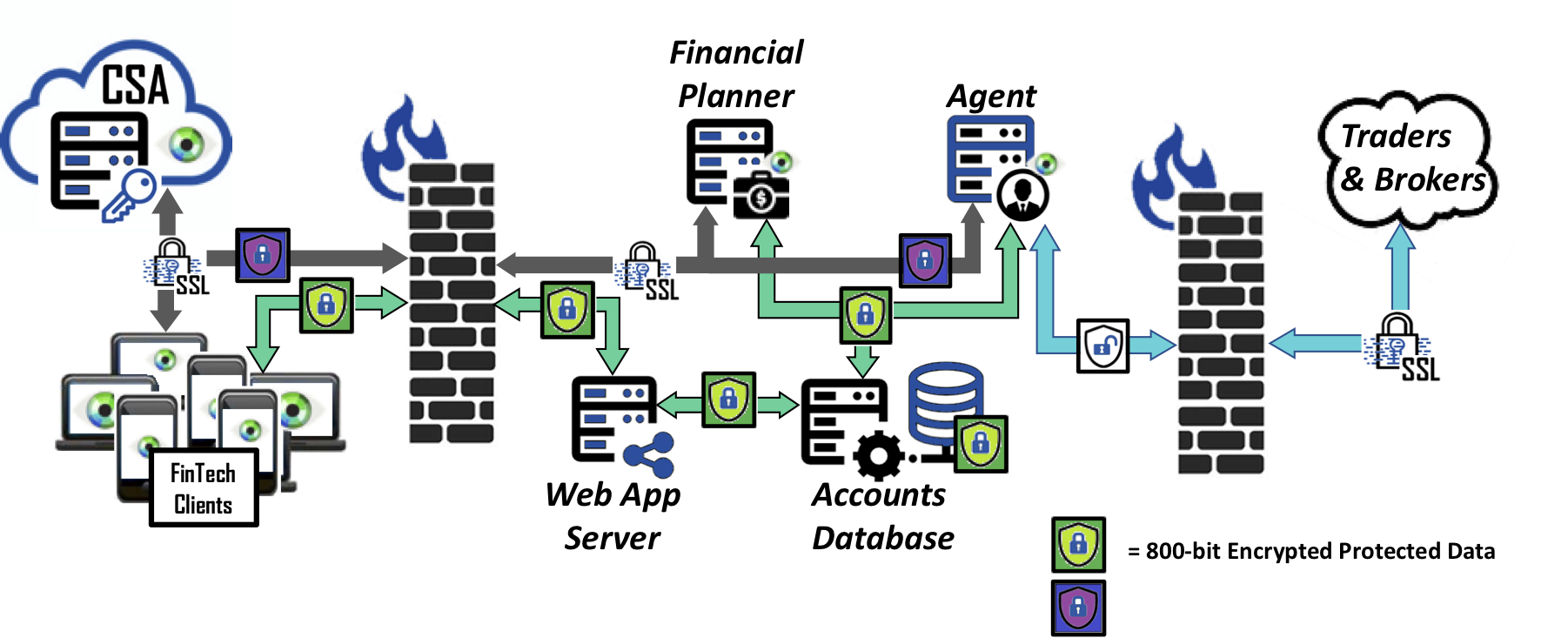
Working in conjunction with existing security products and processes, the best practice to ensure data protection even after a breach is to encrypt customers’ PII data so that cyber criminals or internal non-authorized users only obtain unintelligible data. Bonafeyed can secure this customer data with the following approach:
- Many Fintech systems proxy access to other systems – those credentials must be kept safe – ideally this is a combination of Bona-Isolator™ and Bonafeyed encryption.
- It may be necessary to allow other systems/countries to access information which can be done by adding them to a Key Group.
- KYC information should be kept behind Bona-Isolator.
- Encrypting data with Bonafeyed’s data protection platform keeps the information safe between the client and backend – because the data is always encrypted.
Taking these steps, it is easy to integrate Bonafeyed into existing systems – simply take what are today’s stored procedures or reporting agents on the database server and move them to a separate machine acting as a client with restricted permissions. In such a case, if there is an error or hack, the exposure to information is contained and limited.
With Bonafeyed, when encrypted data is lost, stolen, abandoned or forgotten, it remains protected and becomes permanently inaccessible once keys are deleted or retired ensuring cyber criminals or internal non-authorized users only obtain unintelligible data, which exceeds the requirements of Gramm-Leach-Bliley Act and money transmitter laws!


▶ Add a new level of data protection for clients
▶ Securely support mobile data access
▶ 143M Equifax accts breached from unpatched web server
▶ FDIC, OCC & FRB agencies impose 36-hr breach notice

Banking Use Case: Small Banks, Community Banks, and Credit Unions
The financial and banking services sector faces almost triple the number of cyberattacks than any other industry today. Core banking solutions help banks reduce operational and support expenses, provide real-time transaction processing, and manage bank accounts by aggregating CRM, ERP and management functions into a centralized database. Infiltrating these back-end processes present cybercriminals multiple opportunities to profit through ransomware and brokering of stolen data.
On or about October 2020, American Bank Systems, a service provider to US banks and financial institutions, was attacked, confronted with ransomware, and subsequently, 53 GB of data leaked. The cyberattack impacted ABS’ clients including small banks, community banks and mortgage companies. The challenge is financial institutions must protect all “nonpublic personal information” relating to current and former customers under the Gramm-Leach-Bliley Act, the Right to Financial Privacy Act, and the Fair Credit Reporting Act. Verizon’s 2020 Data Breach Investigations Report found, “The majority of attacks in this sector are perpetrated by external actors who are financially motivated to access easily monetized data stored by the victim organizations” and the top vulnerability is web applications using stolen credentials followed by a misconfiguration of IT. The fact is once the perpetrators acquire access to the databases, they obtain banking records with PII, loan, customers’ Tax ID or SSN information.
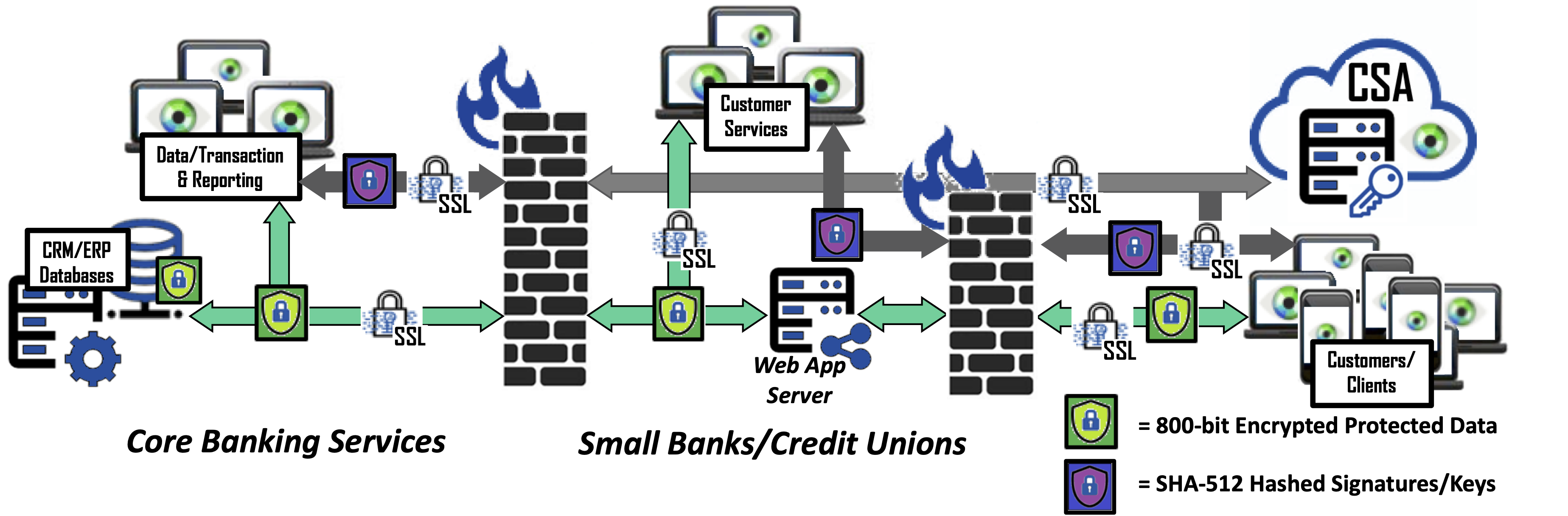
Applying Bonafeyed’s Data Defined Security to banking services, core computer backend databases can safeguard data with field and columnar level data encryption while allowing banks and customers to securely access the data using their existing systems. This ensures in the event of a breach monetary exploitation of the bank’s and client’s data is not possible. In other words, querying the databases would only yield encrypted data that has no value.
Bonafeyed also protects banking data on less complicated security systems over mobile devices by simply taking existing store procedures or reporting agents on the database server and isolate them as a separate client with diversified decryption. In such a case, if there is a leak or breach, the exposure to the vast amounts of PII records is limited.


▶ 25% increase in 2020 Healthcare data breaches
▶ Healthcare Web App attacks have increased by 51%
▶ EyeMed exposed 100Ks Aetna, BlueShield & Tufts PHIs
▶ Surpass HIPAA Privacy Requirements

Healthcare Use Case: Protected Health Information under HIPAA
Enacted in 1996 by the Department of Health and Human Services (“HHS”), the Privacy Rule regulates the use and disclosure of protected health information (PHI) by the Healthcare industry.
Healthcare is a lucrative target for cybercriminals who exploit misconfigured IT infrastructure and applications by using attacks such as weaponized ransomware and phishing emails. In the last 10 years, cybercriminals successfully accomplished and often monetized 2,181 healthcare data breaches. Those breaches resulted in the theft/exposure of 176,709,305 healthcare records - equal to nearly half the population of the United States. Healthcare data breaches are now reported at a rate of more than one per day. The largest in 2018, UnityPoint Health notified 1.4 million patients their records may have been breached when its business system was infiltrated. Sadly, this was the second breach for UnityPoint where phishing attacks at their Madison campus breached the data of 16,000 patients five months earlier. In all cases, the problem arises from the common practice of creating concentric layers of security as an attempt to keep attackers out rather than using a data-defined protection approach to directly protect the data.
On the other side of the coin are internal threats. Breaches are often attributable to the use of personal mobile devices in the workplace. BYOD policies have created new vulnerabilities in which up to 80% of healthcare providers use smartphones, tablets, or laptops to support their workflows. According to a survey conducted by Health Information Trust Alliance, 41 percent of PHI breaches are attributable to the theft of an employee´s mobile device or portable media.
Deploying Bonafeyed’s technology in Healthcare database backed applications, encrypts patients’ PHI in real-time and the data remains protected when accessed by authorized staff, accountants, physicians, or registered nurses at terminals or on mobile devices. In addition, patient data placed in backend ERP systems, shared in the cloud, or archived remains protected.
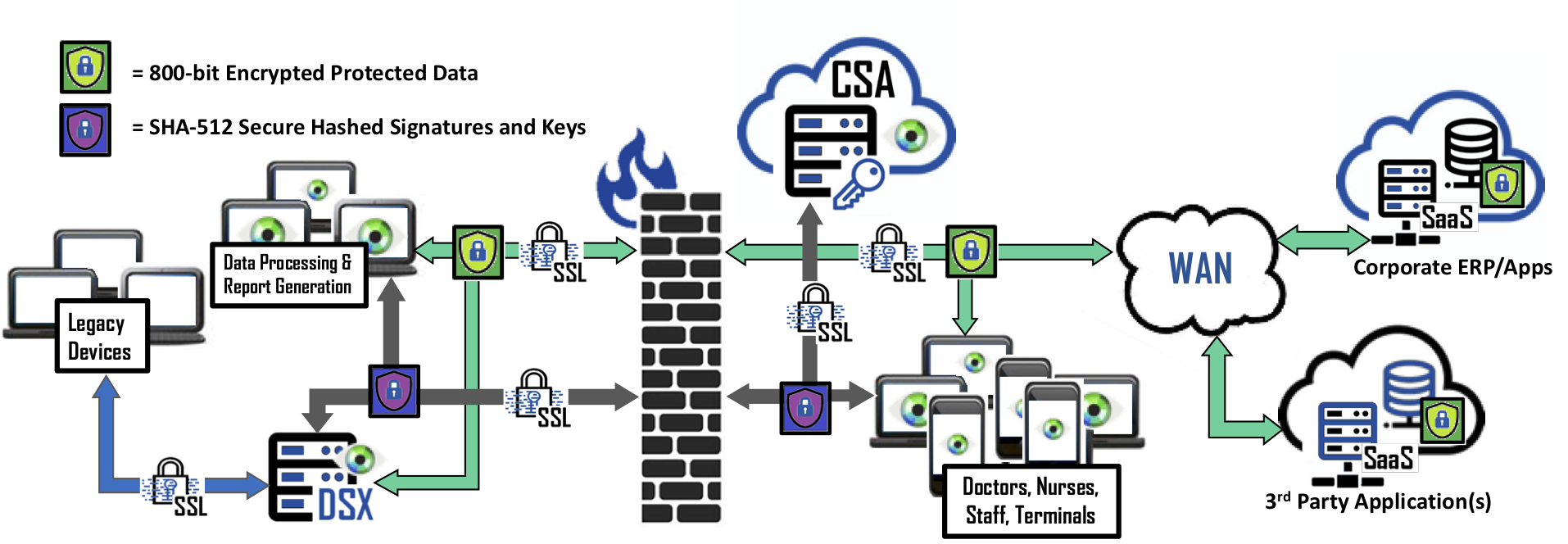
Furthermore, the Data Security Gateway (DSX) facilitates the fastest deployment option for legacy devices or applications without the need for endpoint plugins or altering applications. Bonafeyed can individually protect PHI data fields within ERP backed databases and with Bonafeyed’s Cy4Secure Arbiter (CSA), it validates and authorizes access to protected data using an 800-bit Stream Cipher or AES256 encryption technologies.
A lost or stolen, unencrypted or non-password protected device is the number one HIPAA violation. When a Bonafeyed data encrypted device is taken, abandoned, or forgotten, its data remains protected, inaccessible and demonetized. Deleting its keys ensures cybercriminals or internal non-authorized users obtain no data, which exceeds HIPAA’s data privacy rule!


▶ Secure data no matter where it resides
▶ One data breach can result in 100’s of lawsuits
▶ 142M MGM resorts guest records found on the Dark Web
▶ Walgreen’s mobile app exposed over 10M PII downloads

Retail Use Case: Demonetizing Exposed Retail Customer Data
In an instant, the Covid-19 Pandemic forced society to change our way of life. After state and local governments shut down businesses and enforced stay-at-home orders, we were forced to basically socialize, conduct business and ecommerce activity from home. Sounds very convenient, but is the information exchanged during mobile commerce, electronic banking, supply chain management, inventory management, Internet marketing, online transaction processing, and electronic data interchange protected? Placing online orders with websites with “https” URLs should give confidence the transaction is secure. Then, why is this Personal Identifiable Information (PII) continually hacked and sold to the highest bidder on the dark web?
Take the recent Avon breach for example. As one of the largest and oldest company in the beauty industry, $5.5 billion in annual worldwide sales and 6.4 million representatives, suffered multiple cybersecurity incidents in 2020. The first, a malware attack, impacted operations and the other reported a 7GB database leaking 19 million records went undetected for nine days on June 12. The unprotected PII data of customers and potentially employees, included full names, phone numbers, dates of birth, emails, and more. Adding insult to injury, it is alleged that a Microsoft Azure cloud server was inadvertently left open to the public with no password or encryption, allowing a vulnerable their Elasticsearch database to be effortlessly breached. Without a doubt, a leaky database is no “happy little accident”. A recent Gartner report cited that, “99% of cloud security failures will be the customer’s fault through 2025, and consequently, misconfigurations will continue to be a leading cause of data leakage across all organizations.”
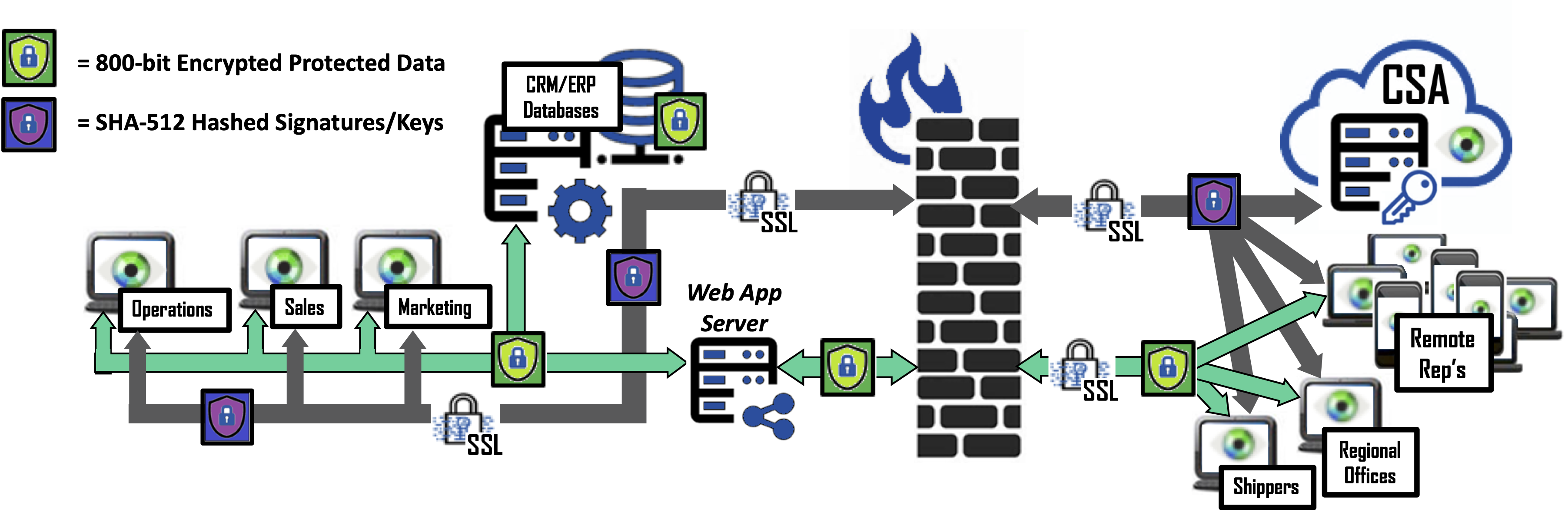
To prevent exploitation and monetization of customer breached data, an organization can leverage Cy4Secure to mitigate their risk and protect its brand. Encrypting data at the source (when users or systems enter data into database driven applications) and keeping it encrypted until it is accessed or read by an authorized user is data defined security. Individual data fields, records, and columns can be encrypted to control access from unauthorized users and manage risk. In Avon’s situation, corporate marketing and sales, regional offices, sales representatives, regional offices and supply-chain partners can search the protected databases with appropriate authorization. Bonafeyed’s data defined security ensures cybercriminals cannot take advantage of leaky databases or open systems . The most they can obtain is unintelligible/encrypted data that has no value on the dark web. “Human Error” is a variable in the technology world and one we must anticipate. Protecting data at the source is the last stand against a data breach.


▶ Over 60% of breaches are caused by third-party providers
▶ Sharing ERP data amongst partners has risks
▶ Mimecast, “Manuf. Industry endured ~24M spam attacks”
▶ Zero trust data-protection for a secure supply-chain

Manufacturing Use Case: Protecting B2B2C
The Manufacturing industry is embracing change on many levels —among the notable trends, companies are shifting to a B2B2C model in an effort to better understand and serve their customers. The industry’s supply chain infrastructure is key and is adopting automated technologies and IT-powered solutions into what some call Industry 4.0. Companies, however, do not operate in isolation. They participate in a global ecosystem where suppliers, value-adding resellers, and trading partners closely collaborate. This is not new. But what is new is the risks associated with collecting and sharing sensitive data driving this digital reinvention. A 2018 study by the Ponemon Institute found that 61% of U.S. companies have experienced a breach “caused by one of their vendors or third parties” —and that number is growing. More than 75% of organizations believe that third-party cybersecurity incidents are increasing. Early in 2020 the FBI sent a cybersecurity alert to the U.S. private sector warning of an ongoing hacking campaign against supply chain software providers. A key contributing factor is the growing complexity of the third-party landscape. As companies increase their reliance on partners, sub-contractors, and suppliers (according to Gartner, 60% of organizations are now working with more than 1,000 third-parties), it’s critical that they manage the risk that these vendors can pose to the business.
The backbone for the Manufacturing industry’s supply chain is the Enterprise Resource Planning (ERP) systems and the databases they contain. ERP systems have evolved to cloud based SaaS solutions that are highly integrated with CRM, MES, MRP, Financial and HR systems, opening a potential gateway for thieves to steal sensitive data about customers and/or employees. Bonafeyed’s Data Defined Security protects this critical data whether on-premises, on the third-party’s premises or in cloud base application. Data protection with diversified encryption can control access on a per record basis or between a manufacture and specific third party. In all cases, the data remains secure even as it moves between network domains and on customers and suppliers end-point devices.
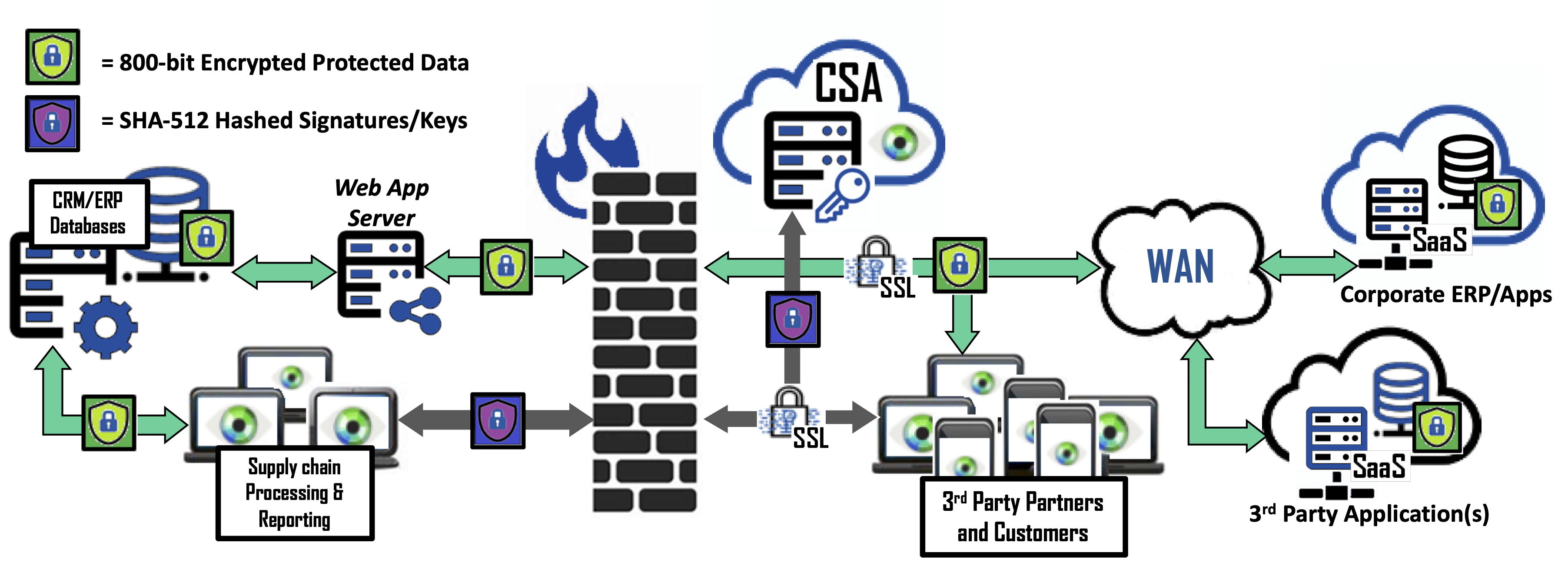
Now more than ever, manufacturing supply chains needs protection, and the ability to receive and supply sensitive information to many different enterprises. From vendors to partners, these digital touch points allow for more efficient and effective operations. In a supply chain attack, a hacker will gain access to a partner or provider that has systems and data access. Through this relationship, the criminals can enter networks, steal data, and cause significant business harm. Bonafeyed demonetizes this shared data and prevents unauthorized access to supply chain data.


▶ Akamai reports video gaming is a growing threat vector
▶ 300K Nintendo accounts breached in 2020
▶ User accounts and payment method is highly prized
▶ Over 2.5 billion gamers across the world

The suspected underlying reasons the gaming industry is the subject of so many breaches begin with video game companies being pushed to use low-friction authentication measures to avoid customer attrition and revenue loss; as with most businesses, time is money and fast paced game release cycles introduce security risks; and finally, the singular focus on games – data security is now an equal priority. Gaming companies have determined that misconfigured servers and insider leaks have enabled the most recent gaming data breaches.
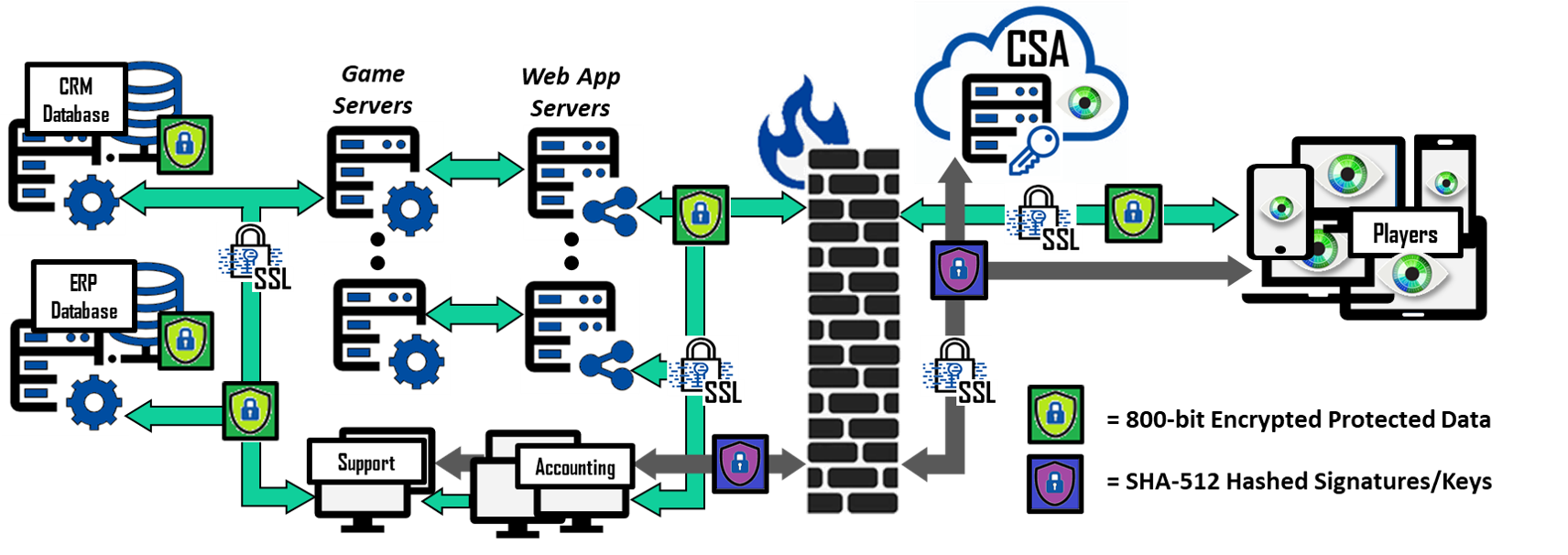
Bonafeyed’s Data Defined Security protects critical data whether in the player CRM databases, the transaction ERP databases or on a gamer’s tablet, PC, or smartphone. A player’s ID (login), password, PII data, and payment information is encrypted by Cy4Secure before it leaves the player’s device and remains encrypted throughout the gaming eco-system, including game servers and databases. Encrypted in-game purchases and billing information can be viewable by the accounting and billing departments. Support and Accounting could access encrypted CRM data. However, not all encrypted fields need to be accessible by all departments or employees. For example, marketing and sales can create reports on demographics, consumption, and revenues, but they do not need to decrypt a majority of the PII or payment information to obtain business analytics. Cy4Secure only allows authorized use of encrypted data.
The gaming world brings joy, fun, and even a learning experience for many players. Protecting personal information has now become as important for game developers as it is for the banking, healthcare, and retail industries. To prevent exploitation and monetization of players’ breached data, developers can use CY4Secure to encrypt data at the source, and keep it encrypted until it is accessed or read by an authorized user. The most cybercriminals can obtain is unintelligible/encrypted data that has no value on the dark web.


