



Finance Use Case: FinTech Customer Information Protection

▶ Protect data behind cloud applications and services
▶ Secure data shared between services
▶ Aggregator platform Cermati.com leaked info of 3M users
▶ Lending app Tokopedia leaked 91M users to the dark web

“Financial companies must….ensure the security and confidentiality of customer information and to protect against unauthorized access to or use of that information, both by third parties and your own employees.”
This means GLB places responsibility for data security directly with the board of directors and for public companies, the Sarbanes-Oxley Act makes the CEO and CFO responsible. With alarming frequency, new reports of serious breaches reveal that concentric or layered security architectures based on detection, protection and transportation technologies are simply inadequate. In many cases human error plays the largest role from misconfiguration, fraudulent scams, and even intentional security violations. Making this problem even more complex to solve, leading global Fintech companies are proactively turning to cloud technology in an attempt to meet increasingly stringent compliance regulations. This is not to say the security challenge is not also faced by historical financial companies since they do offer Internet-connected customer services. Nevertheless, any data breach, no matter how small, can result in direct liability to a company and its officers.
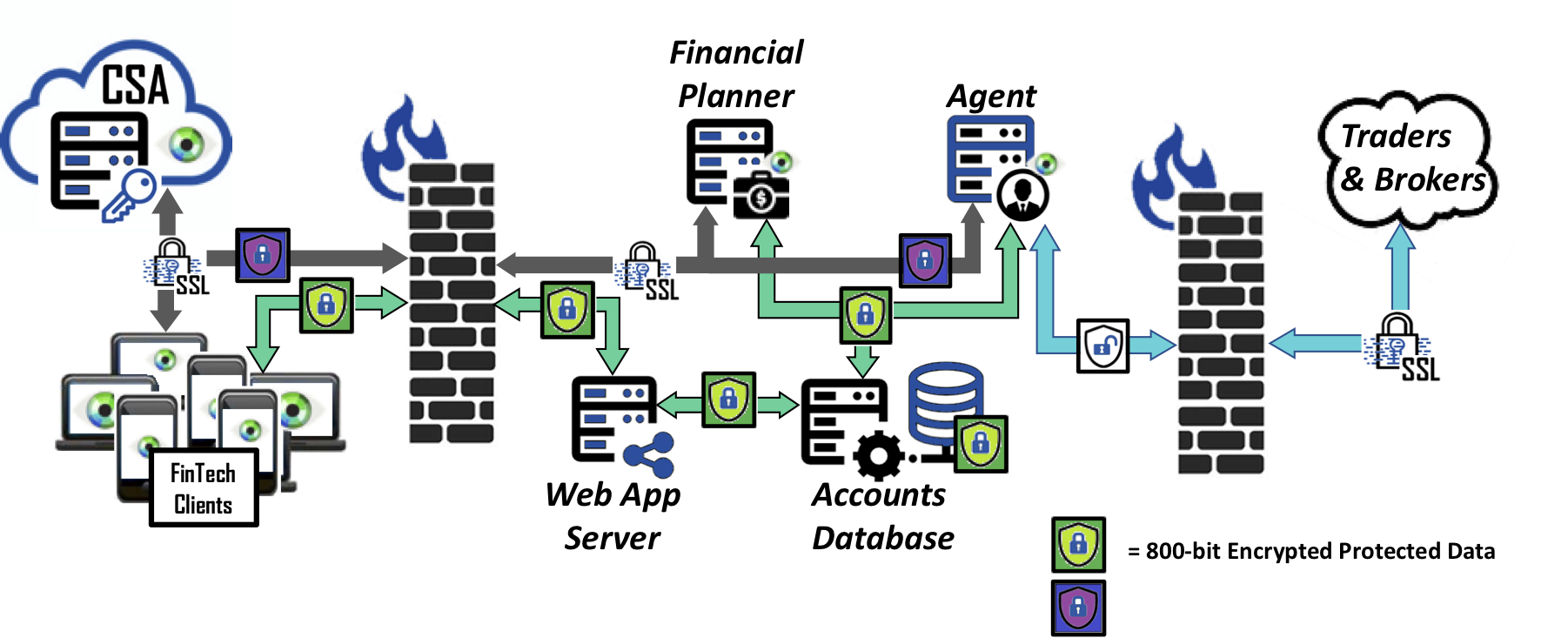
Working in conjunction with existing security products and processes, the best practice to ensure data protection even after a breach is to encrypt customers’ PII data so that cyber criminals or internal non-authorized users only obtain unintelligible data. Bonafeyed can secure this customer data with the following approach:
- Many Fintech systems proxy access to other systems – those credentials must be kept safe – ideally this is a combination of Bona-Isolator™ and Bonafeyed encryption.
- It may be necessary to allow other systems/countries to access information which can be done by adding them to a Key Group.
- KYC information should be kept behind Bona-Isolator.
- Encrypting data with Bonafeyed’s data protection platform keeps the information safe between the client and backend – because the data is always encrypted.
With Bonafeyed, when encrypted data is lost, stolen, abandoned or forgotten, it remains protected and becomes permanently inaccessible once keys are deleted or retired ensuring cyber criminals or internal non-authorized users only obtain unintelligible data, which exceeds the requirements of Gramm-Leach-Bliley Act and money transmitter laws!

Banking Use Case: Small Banks, Community Banks, and Credit Unions

▶ Add a new level of data protection for clients
▶ Securely support mobile data access
▶ 143M Equifax accts breached from unpatched web server
▶ FDIC, OCC & FRB agencies impose 36-hr breach notice

On or about October 2020, American Bank Systems, a service provider to US banks and financial institutions, was attacked, confronted with ransomware, and subsequently, 53 GB of data leaked. The cyberattack impacted ABS’ clients including small banks, community banks and mortgage companies. The challenge is financial institutions must protect all “nonpublic personal information” relating to current and former customers under the Gramm-Leach-Bliley Act, the Right to Financial Privacy Act, and the Fair Credit Reporting Act. Verizon’s 2020 Data Breach Investigations Report found, “The majority of attacks in this sector are perpetrated by external actors who are financially motivated to access easily monetized data stored by the victim organizations” and the top vulnerability is web applications using stolen credentials followed by a misconfiguration of IT. The fact is once the perpetrators acquire access to the databases, they obtain banking records with PII, loan, customers’ Tax ID or SSN information.
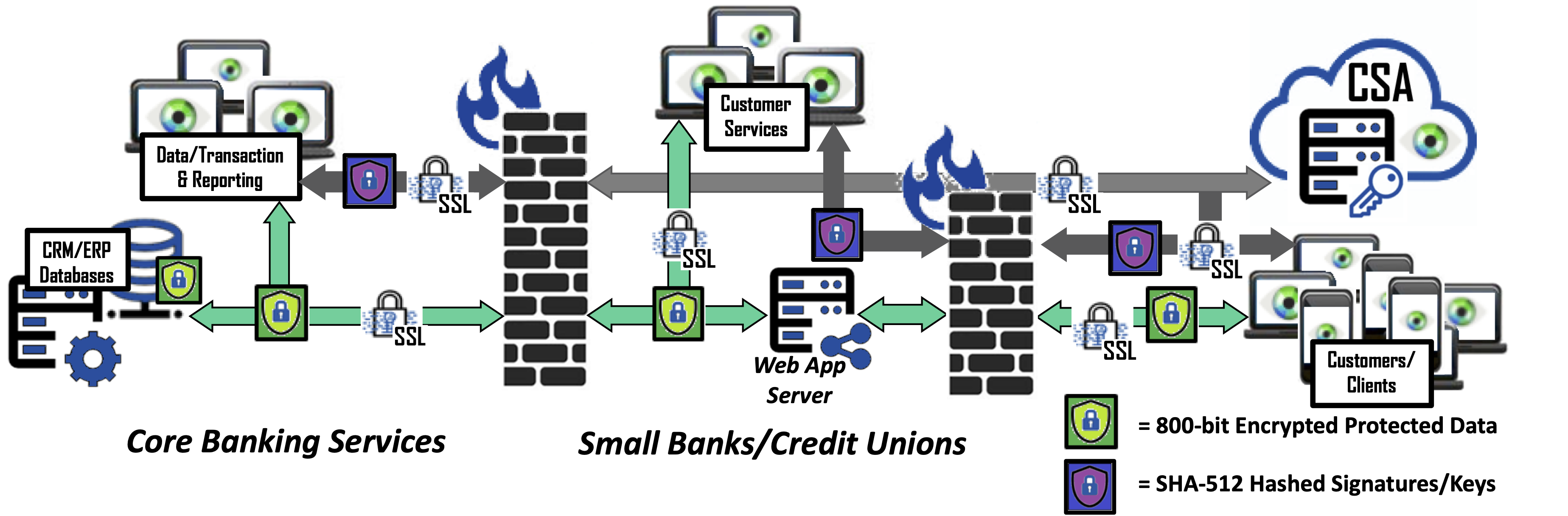
Applying Bonafeyed’s Data Defined Security to banking services, core computer backend databases can safeguard data with field and columnar level data encryption while allowing banks and customers to securely access the data using their existing systems. This ensures in the event of a breach monetary exploitation of the bank’s and client’s data is not possible. In other words, querying the databases would only yield encrypted data that has no value.
Bonafeyed also protects banking data on less complicated security systems over mobile devices by simply taking existing store procedures or reporting agents on the database server and isolate them as a separate client with diversified decryption. In such a case, if there is a leak or breach, the exposure to the vast amounts of PII records is limited.


